I've just finished a proof-of-concept and I'm looking for feedback.
The world takes place in a terminal and the user hacks through systems for some end goal (the first scenario is to hack your way through a network and kill a drone passenger by killing the drone's autopilot). The user discovers/purchases exploits (future) which can then be used on systems to gain control over them. One of the areas I find difficult is balancing measures vs. counter-measures, though this simple prototype doesn't get there yet.
Levels will be defined by networks that have collections of interconnected systems that can be hacked, allowing access to systems deeper in the network (the target).
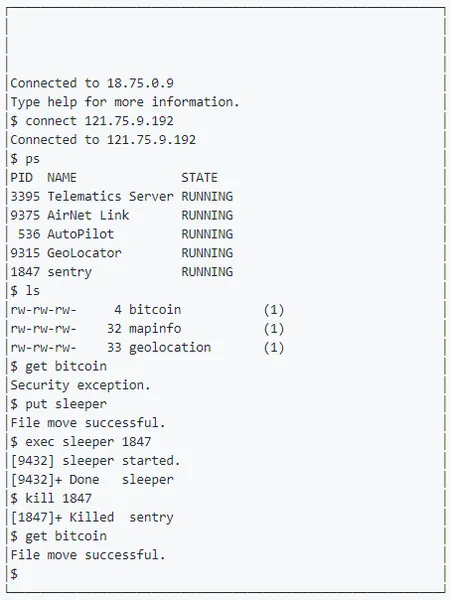
It's developed in C on Linux (using ncurses). The image shows illustrates a sample scenario for stealing bitcoin from a system. Full source is available at https://github.com/mtimjones/spectre.
Thanks,
Tim.